Layer security and technology strategies to keep your people and property safe

First in a series based on the IMEG executive guide, “Holistic Security Design: Mitigate vulnerability, reduce risk, and keep people safe.”
By Ryan Searles
| View an interactive 3D graphic that shows the various security measures that can be applied to a hospital. These strategies can be applied to any building type and customized to meet a client’s needs. |
To create a safe environment, the security design of a new facility or campus must go beyond basic camera and access control devices to a holistic approach that blends security strategies with technology.
This approach evaluates everything from the layout of hallways and exterior sight lines to the fencing or vegetation used at the perimeter of the property, in addition to the technology typically used for security cameras, access control systems, and visitor management. Each strategy plays a role in providing the optimum safety for your building, people, and assets.
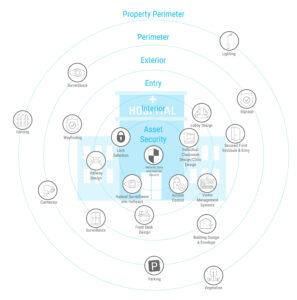
Blending security and technology design involves all aspects of a site and the facility. An effective security design provides layers, or concentric circles of security. Each circle encompasses an aspect of security and technology, such as cameras, access control, building envelope, landscaping, Crime Prevention Through Environmental Design (CPTED) principles, and more. All these circles work in tandem to provide an all-encompassing security plan.
As shown in the concentric circles graphic, various solutions are suggested at each level of security. Some strategies include:
- Vegetation and perimeter fencing to set territorial boundaries
- Sufficient parking lot lighting
 Open spaces for unobstructed sight lines to provide natural surveillance
Open spaces for unobstructed sight lines to provide natural surveillance - Open sitting areas to encourage more watchful eyes in public spaces and deter crime
- Purposeful architectural elements that prevent loitering in public spaces
- Clear wayfinding throughout the property, inside and out
- Natural access control at the front entry
- Efficient use of security cameras
- Secured front vestibule & entry
- Material, data, and individual security
Designers and owners should work together to identify the options within each circle that work best for their specific project and create a plan to implement these solutions.
For more information, download a copy of the IMEG executive guide, “Holistic Security Design: Mitigate vulnerability, reduce risk, and keep people safe.”
Check out other blogs in this series:









 Open spaces for unobstructed sight lines to provide natural surveillance
Open spaces for unobstructed sight lines to provide natural surveillance